What is Phishing?
Gone phishing? Cybercriminals sure have, but it’s not just catch and release anymore. At its core, phishing is a cybercrime that uses electronic communication to take advantage of users. Attackers attempt to gain sensitive or confidential information, such as usernames and passwords, credit card information, and more by posing as legitimate organizations or individuals. They use social engineering to manipulate victims into clicking on malicious links and entering information.
As we head into the second half of 2023, the threat of malware attacks continues to remain a critical concern for businesses of all sizes. 91% of cyber attacks starts with a phishing email. It is still the top way phishing tactics are delivered, with 96% arriving in an inbox; however, there are other social engineering tactics outside of email that are being used every day. We’ve broken down these differences below:
Why is email such an easy target? While most people know how to send and receive emails, the same cannot be said about the understanding of how emails are sent or received. The simplicity of modern email interfaces lulls users into a false sense of security; however, a potent combination of human error and malicious agents can make emails one of the most dangerous threats to an organization’s security.
As with all security practices, it starts with training employees to understand and identify suspicious emails. Alongside this training, organizations need to have the right tools to fight against this data theft, including anti-virus filters, email filtering, email encryption, and more.
Types of email phishing can be broken down into the following categories:
- Spear phishing: These attacks will not look random. Attackers will gather information about the victim to make the email feel more authentic. Of social engineering attacks like spear phishing, 65% are sucessful.
- Clone Phishing: Attackers will make almost identical copies of previously delivered email messages and change an attachment or link to something malicious.
- Whaling: These specifically target high profile and/or senior executives at organizations, presenting themselves as legal communications or other executive business matters.
Other Forms of Phishing
While most phishing attempts do occur over email, it is still common to receive material in other ways. A telephone attempt is also known as vishing. When a message is sent over text message, it is called smishing.
Phishing is an Epidemic
Every day, evidence of 560,000 new pieces of malware is detected. With over one billion malware programs in existence, businesses are facing security attacks and epidemic proportions. In the past decade, there has been an 87% increase in malware infections, primarily attributed to phishing attempts. With the cost of cyber crime expected to reach $8 trillion this year, protecting your company’s data against ransomware attacks needs to be a top priority. Every minute, four companies fall victim to ransomware attacks with the high cost of of loss of sensitive data, financial loss, damaged reputation and legal ramifications.
8 Ways to Identify Phishing Attempts
- Requests for Sensitive Information – A legitimate organization will never ask you to enter any information that is sensitive by following a link. You will usually be asked to go to the official website or app to enter your credentials and any other information that is required.
- Generic Salutations – Most hackers will greet you with a “Dear Valued Customer…” or “Dear Account Holder.” Sometimes, ads will not even include a greeting. Genuine organizations will use your name.
- Check the Domain – Don’t just check the name of the sender. Check the email address attached by hovering over the ‘from’ address. If you see any changes from what you were expecting, like numbers or letters added, this might be a phishing attempt.
- Bad Grammar – Legitimate organizations will send emails that are professionally written, with no spelling errors or bad syntax. Hackers believe their prey are less observant and easier targets, so they tend to have spelling errors and grammatical mistakes.
- Forcing you on to a Site – If in doubt, don’t open the email. Many times, emails can be coded entirely as a hyperlink so any accidental click anywhere in the email can lead you to a malicious site or start a spam download on your computer.
- Unsolicited Attachments – Authentic organizations will seldom send you attachments. They will usually direct you to their website to download what you need from there.
- Hyperlinks – Always hover over any links in the email because it may not be all it appears to be. When you hover over the link, it will show you the actual URL it will direct you to.
- Sense of Urgency – One of a hacker’s favorite methods to hook a victim is asking them to act fast, often by offering a one-time deal for a limited time. Other times they will pretend to inform you that your account has been compromised. It is usually best to ignore these communications.
Here’s an example…
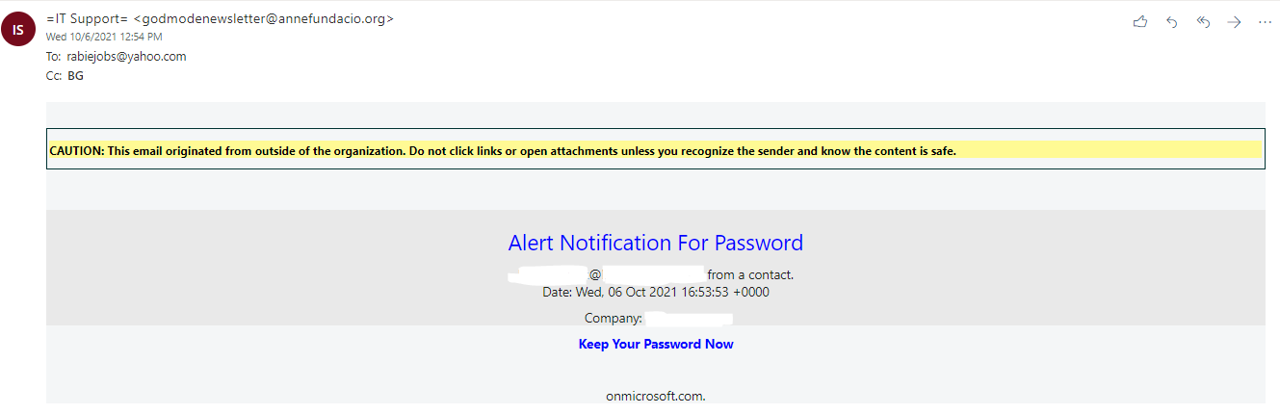
(Note – we have removed our domain information we tested here as not to advertise what services we use for which of our testing email domains. This email was from a testing domain used at O365.)
This was an email we recently received at one of our email domains. Here’s how we know this is a phishing attempt:
-
- Yellow Headers: We added headers from our email provider, letting the receiver know it did not source from our domain. If your provider offers such potential, this is a great tool that could benefit your team’s awareness of where an email is coming from.
- “To” and “From” Visibility: We see that “To” and “From” are not domains that anyone should expect to see regarding a password alert. This email is hoping that the user has an urgency to click the “Keep your Password Now” link and ignore the rest of these details.
- The onmicrosoft[.]com message at the bottom looks out of place and is likely not an email that you would receive for a password reset notification from Microsoft.
When we went to “View Message Details” on this specific email, here is what stood out:
“Received: from 365days[.]one – Marked by some Web Filtering Vendors as Placeholder Category
X-Originating-Ip: Received-SPF: pass (domain of mail110.suw91.mcdlv[.]net designates 198.X.X.X as permitted sender) – IP address of the user that sent the email, then using that identify the owner of the IP address, leveraging sites like ARIN Whois/RDAP.”
Buried in the headers we found:
“X-Mailer: MailChimp Mailer – **CIDEXAMPLE** X-Campaign: mailchimp CIDEXAMPLE X-campaignid: mailchimp CIDEXAMPLE X-Report-Abuse: Please report abuse for this campaign here: https://mailchimp.com/contact/abuse/?u= CIDEXAMPLE &id= CIDEXAMPLE” and since this is not new to use services, such as MailChimp for such activities, MailChimp does have a website using the above abuse link to report it (we removed all indicators from this campaignid above, but this is an example).
While this specific email did source from MailChimp, it was forwarded by another email service provider before reaching our test email address domain. In this example, we found our email report to MailChimp as Abuse returned a quick response back.
Lessons Learned:
-
- Mismatched sender addresses? This may not always be an indicator of malicious intent, but helpful to review.
- Email Travel Path? As email traverses’ multiple email servers a record of those servers is stored in the email headers. Headers can be modified by email servers so should not be considered entirely trustworthy. This is where looking for DKIM and SPF being enabled will show results of “failed verification.”
- Email client specified? Most of us use a client to send our email and do not directly connect, but as with the email travel path, email client can also be altered or spoofed.
- Received an email with an attachment? Call the person directly if possible, or craft a new email to them (not using the reply button) and ask about the attachment.
- Received an email with a link? If it’s a system you normally use, don’t click the link, use a trusted process that doesn’t involve clicking the link. For example, if you use Gmail and received a Gmail expired password email: open a new browser, type in the domain on your own, log in, and verify the password works. While you are logged in, check your Google Security settings to see if any strange systems or IP addresses connected to the account recently that would lead to receiving such an email. That’s just one example, but if you use a Portal to access corporate tools, use a Web Portal of Widgets to access the site (via Lastpass, Okta, PingIdentity, OneLogin to name a few).
Pro Tip: Don’t publicly share templates for emails (or communication emails) which help adversaries better craft attacks against your organization.
Helpful Links
These links include tools and quizzes to ensure you’re up to speed on phishing knowledge!
https://www.dmarcanalyzer.com/dkim/
https://phishingquiz.withgoogle.com/
https://www.intradyn.com/phishing-quiz/
https://www.ftc.gov/tips-advice/business-center/small-businesses/cybersecurity/quiz/phishing



