Key Consideration #1 – Understand NIST 800-171 and where you are as a company.
Before taking on any new project, the first goal should always be to reflect on where you currently are as a company and where you would like to be in the future. If you are looking for starting point, ask these evaluation questions:
- What is NIST 800-171?
Understanding the complexities of obtaining NIST 800-171 compliance gives you the knowledge of what needs to be met. Currently, it contains 110 security controls across 14 categories.
Key NIST Concepts:
-
- Scope- Refers to what systems and networks are included in an assessment (your entire network may or not be “in scope”).
- Projects
- Gap Analysis- A gap assessment helps an organization find gaps in their network and solutions to fill them. Learn more about our Complete Gap Assessment.
2. Are you familiar with what CUI is?
Controlled Unclassified Information is a type of marking used by the federal government to identify information and confidential data that is not classified, yet requires protection from unnecessary disclosure (ie. Financial records, PII, FOUO).
3. Have you defined a timeline?
With the knowledge you have gained about NIST 800-171, plan out a realistic timeline to implement controls and Plan of Action & Milestones (POAMs). Hint – this will take longer than you think! Ensure that ample time is given to accomplish tasks to best allocate time and realistic expectations. Overall, a gap analysis is critical in understanding what needs to be accomplished and potentially how much that will cost.
Next, make sure you have the full support of management. Completing a NIST 800-171 System Security Plan will require contributions from other parties within your organization, including HR, management, and security.
4. Do you have funding?
Working through NIST 800-171 compliance requires a great deal of time and effort. This may require purchasing and implementing new products to meet requirements. Bringing in consultants to assist will also require additional funding, but an expert can really help your organization meet the requirements in a timelier fashion. If management has made a commitment to provide funding where necessary, then it is far more likely to lead to successfully attaining NIST 800-171 compliance.
There are, however, different avenues to receive funding. For our local Maryland organizations, the Maryland Defense Cybersecurity Assistance Program (DCAP) provides funding and assistance for defense contractors to comply with the DFARS and NIST 800-171 standards for cybersecurity. The program provides funding and resources to comply with the cybersecurity standard and is funded by the Department of Defense’s Office of Economic Adjustment (OEA) through the Maryland Department of Commerce.
If you are a Maryland company, funding through this program is limited – learn more about how we can help you get funding or reach out to us today!
5. Do you have technical and management staff to dedicate based on your goal date for completion?
Assigning employees with projects and tasks is critical to tackling NIST 800-171 compliance. This will require help from management regarding projects, tasks, and owners so that progress can be accomplished efficiently.
6. Do you have mature policies and procedures?
NIST/CMMC covers both administrative and technical aspects, which require defined expectations. Do not be fooled into thinking that NIST 800-171 is an IT only compliance. For example, malware protection mechanisms are a technical implementation which will satisfy a control; however, policies and procedures will dictate how the organization implements malware protection mechanisms and helps prove that this is consistently applied and part of standard operating procedures.
7. Is management ready to conduct a Risk Assessment?
Risk assessments play a significant role in not only satisfying the risk assessment domain controls, but also in implementing security controls where they are needed. Has your organization conducted a risk assessment? Planning to? Does it make sense to bring in a third party consultant to assist?
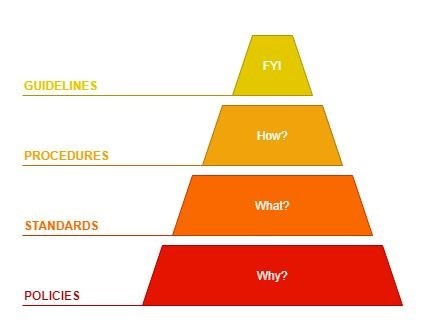
Key Consideration #2 – Understand the importance of document hierarchy.
Documentation hierarchy is important to dictate the expectations of management and ensure consistency of employee actions. It states why something needs to be accomplished and to what degree, while providing specific instructions on how to accomplish it. Assessors will be looking to determine that organizations satisfy NIST 800-171 controls and that regardless of employee rotation or turnover, implementations and actions are consistently meeting the expectations set forth in policies.
Policies -> Standards -> Procedures -> Guidelines
- Policies – A set of expectations with general management statements. They answer the question, “why do I need to do this?”
- Standard – Provides specific, mandatory controls. Answers the question, “what is required?”
- Procedure – Step by step instructions on how something should be accomplished. Answers the question, “how do I do it?”
- Guideline – FYI supplies and added recommended guidance (recommendations/best practices).
What is the difference between policies and procedures?
Policies and procedures make up the backbone of what expectations are set forth by management and what should be accomplished at a prominent level. Policies are set of rules and expectations for an organization through which personnel are expected to follow to achieve a set of goals. Procedures will back up these policies by dictating how certain processes should be accomplished.
How do you determine which controls require documentation and which ones require technical controls?
Many requirements will need both a technical solution and documentation, which should include policies and procedures. For most technical solutions, policies/procedures will still be required to prove that the company is satisfying the requirements of NIST 800-171. Evidence is an important aspect of proving compliance, and documentation makes up a large part of showing that your organization has cybersecurity maturity. CMMC (Cybersecurity Maturity Model Certification) Level 3 will require that companies have been satisfying these requirements and it is part of the company culture and standard operations. As you read through and understand the requirements, it is important to understand whether it makes sense for your organization to implement just an administrative control via documentation (i.e., policies and procedures that dictate how certain functions should be compliant) or to implement a technical control through technology.
What is the best way to approach documentation in a way that is right for your organization?
Addressing documentation starts with having realistic expectations when it comes to what your organization can accomplish. To do this, evaluate what current policies/procedures you have and where to add additional language to satisfy the controls or create new documents. Then, you can acknowledge your core requirements and establish how best to write expectations and processes that fit in with the company culture and structure. This may require employees taking on new responsibilities and implementing new procedures that have not previously been done.
Key Consideration #3 – Leveraging technology to satisfy controls.
Most of NIST/CMMC can be satisfied with non-technical administrative means, but that does not mean it is a good approach for your organization; therefore, to implement in the best way possible, understand what controls need technical solutions and which ones need technical and non-technical implementations.
Which technologies/solutions check off the most controls?
Before looking into new tools, maximize the tools/apps you currently have. Take stock of what tools, systems, and applications are already deployed within the environment that could be configured to satisfy NIST 800-171 controls. If you have already paid for something that just needs to be configured, this will reduce costs and allow for better investment on other needed technologies. Then, after assessing your current environment, purchase new ones where they are needed. It is also cost saving to look for a provider that can maximize your investment by providing tools as part of a package.
Common Technologies:
- SIEM/SOC – The most logical technical solution to satisfy many of the NIST 800-171 controls is to implement a SIEM (Security Information and Events Management) solution. It is easy to assume that this is something that can be done internally by an IT department. However, the depth of skill, cost to implement, and the level of resources required to successfully to do this is unrealistic for most organizations. SIEM systems are expensive, require countless hours of tuning, and need specially trained analysts that command large salaries. The better option is to offload this to a 3rd party SOC (Security Operations Center) provider that will be able to provide a valuable service for a fraction of the cost.
- Active Directory – There are numerous controls that can be satisfied by just configuring different policies within Microsoft Active Directory Group Policy. The time and effort to implement these policies goes a long way and requires little up-front cost; but, be aware that documentation of policies, procedures, standards, and guidelines will still be necessary to show the maturity of the organization.
Know where Your Data is, who is handling it, how it is being processed – understanding the scope of your SSP (System Security Plan).
- Where is your data? SaaS (Software as a Service), IaaS (Infrastructure as a Service), and other cloud infrastructure services give organizations great flexibility in storing data outside the physical office, which presents additional challenges regarding NIST 800-171 compliance and implementing the appropriate controls. Having a solid understanding of where data is stored, transferred, and processed within cloud services is key to ensuring the right systems and services are within the scope of controls.
- Who is handling your data? Which employees, departments, contractors, etc. will have access to sensitive CUI data. Has your organization thoughtfully prepared appropriate access controls to data?
- How is your data being processed? Where does your data flow through? Creating a data flow diagram with the owners of that data can paint a clearer picture of your data’s path through an organization. With a clear picture, it becomes more obvious what may be in-scope and where to apply the appropriate controls.
- Understanding the scope of your System Security Plan – What aspects of your system are in scope and what is not in scope? This will determine the extent to which NIST 800-171 controls need to be implemented. Depending on the size of your organization and network, it may be more effective to just consider the entire LAN (local area network) to be in scope. Additionally, if your organization is utilizing cloud services which CUI data is transported, stored, or processed through then that will put those cloud services in-scope.
Challenges will be presented for the domains of Access Control, Audit and Accountability, System and Communications Protection, and Configuration Management. Understanding these challenges and how to overcome them will be the key to success in ensuring your organization is NIST 800-171 compliant and prepared for CMMC accreditation.
At Braxton-Grant, we are here to identify and resolve hidden gaps in your network. If you are ready to take the next step in becoming NIST 800-171 compliant, reach out to us and let us be your trusted advisor.
Braxton-Grant’s 3-Step Cyber Assessment
Braxton-Grant is a cybersecurity consulting organization with NIST SP 800-171 Subject Matter Experts and CMMC Registered Practitioners to assist in pre-assessments for organizations with DoD contracts.
We have developed a low-cost solution to help companies get compliant quickly and stay compliant without disrupting your budget.