Understanding Key Identity and Access Management Components
Identity and Access Management (IAM) is the ability to provision, manage, audit, and secure digital identities while facilitating authentic connections to view company assets. IAM applies these provisions whether employees are located on-premises, the cloud, or based on the roles assigned to each digital identity.
IAM addresses the mission-critical need to ensure appropriate access to resources across increasingly heterogeneous technology environments and compliance requirements. IAM is increasingly business-aligned and requires business skills, not just technical expertise. Enterprises that develop mature IAM capabilities can reduce their identity management costs and, more importantly, become significantly more agile in supporting new business initiatives.
The IAM flow can be displayed like this:
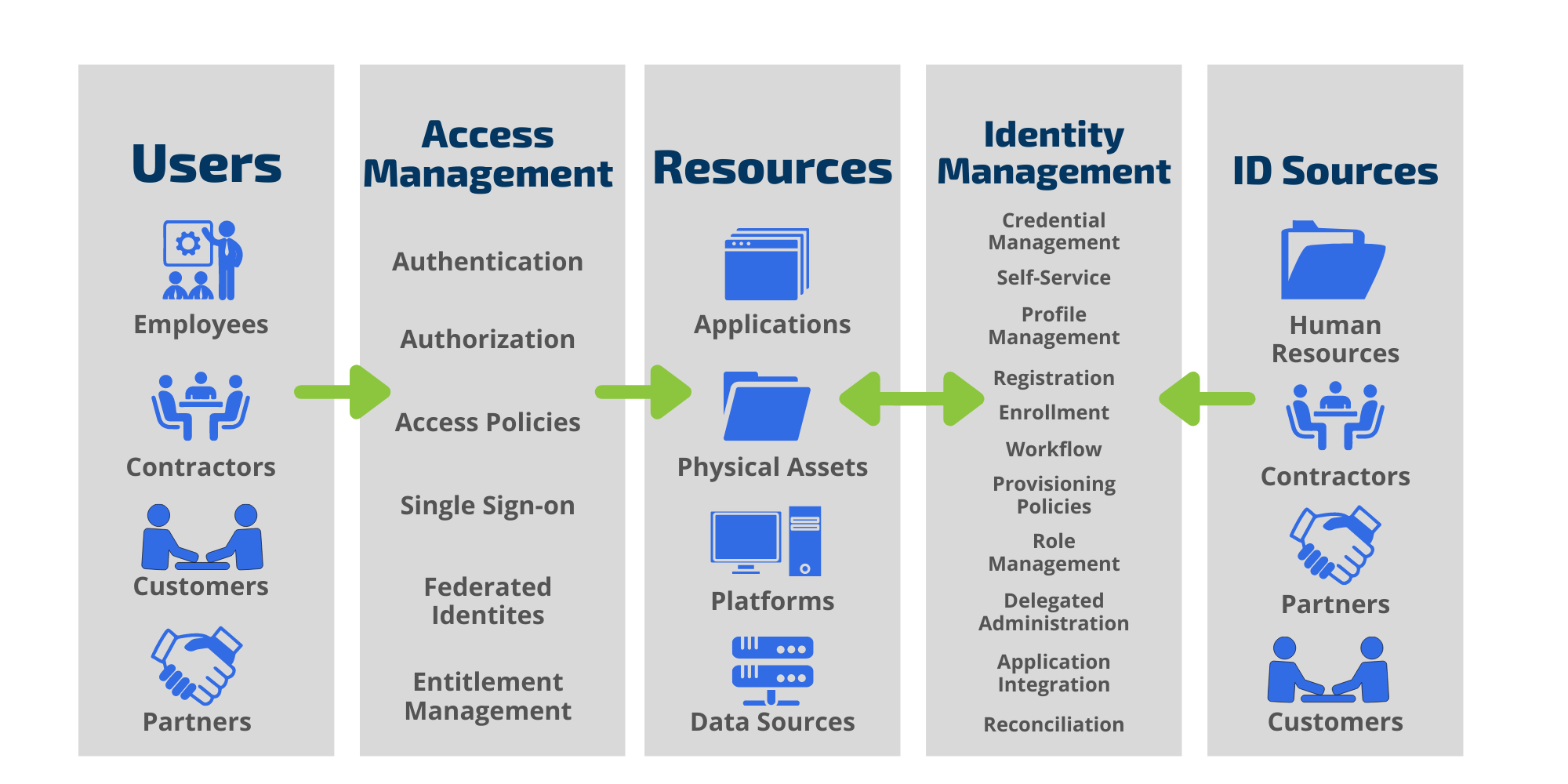
Gartner defines IAM as “the discipline that enables the right individuals to access the right resources at the right times for the right reasons.” They highlight top priorities for IAM, including:
- Clear vision and strategy for developing or building an IAM program.
- Use of Multifactor Authentication (MFA).
- Identity Governance and Administration (IGA).
- Privileged Access Management (PAM).
- Cloud IAM.
We identify the essential Identity and Access Management Components as:
- Customer Identity and Access Management (CIAM).
- Multifactor Authentication (MFA).
- Privileged Access Management (PAM).
- Identity as a Service (IDaaS).
- Single Sign-on (SSO).
- Passwordless Authentication.
Let’s break these down to understand how they fit into Identity and Access Management:
What is CIAM?
While IAM traditionally focuses on securing what your company’s workforce has access to, it is also used to manage your customer digital experience. This is also called Customer Identity and Access Management (CIAM).
CIAM manages the authentication of customer identities; therefore, it is necessary for public-facing applications that require account registrations.
Key CIAM features include…
- Self-service for registration.
- Password and consent management.
- Profile generation and management.
- Authentication and authorization into applications.
- Identity repositories, reporting, and analytics.
- APIs and SDKs for mobile applications.
- Social identity registration and login.
What is MFA?
Multi-factor Authentication (MFA) is an authentication method that requires users to provide two or more verification factors to gain access to a desired resource. MFA can be used for applications, online accounts, or a VPN. MFA is also often linked to a Zero Trust implementation.
MFA is a core component of a strong IAM policy. Rather than just asking for a username and password, MFA requires one or more additional verification factors, which decreases the likelihood of a successful attack. Each piece of evidence must come from a different category: something they know, something they have or something they are.

What is PAM?
Privileged Access Management (PAM) protects identities with exclusive access or capabilities beyond a normal user, such as an administrator. Privileged accounts must be protected due to accounts having additional capabilities and/or confidential information.
The first step in implementing PAM is to determine which accounts have privileged access. Then, you can set up your policies based on that hierarchy.
As a component of IAM, PAM protects access privileged identities; however, IAM offers its other components (MFA, IDaaS, SSO, Passwordless Authentication) for all accounts, not just ones with privileged access.
What is IDaaS?
Identity as a Service (IDaaS) can help you reduce risk and avoid unneeded IT infrastructure costs by providing cloud-based authentication built by a third-party provider. IDaaS providers supply cloud-based authentication or identity management for their customers.
According to Gartner, the core aspects of IDaaS are:
- IGA: Provisioning users to cloud applications and password reset functionality.
- Access: User authentication, SSO, and authorization supporting federation standards such as Security Access Markup Language (SAML).
- Intelligence: Identity access log monitoring and reporting.
What is SSO?
Single sign-on (SSO) provides the capability to authenticate once, and then be automatically authenticated when accessing various target systems. It eliminates the need to separately authenticate individual applications and systems.
Through SSO, target applications and systems still maintain their own credential stores and present sign-on prompts to client devices. Behind the scenes, SSO responds to those prompts and maps the credentials to a single login/password pair.
What is Passwordless Authentication?
Passwordless Authentication verifies users without a password. Using password verification has been around for decades and is a common security standard; however, passwords can also be very unreliable because they can be easily guessed, lost/forgotten, or stolen. Passwords are the top target of hackers.
Passwordless authentication replaces passwords with other authentication factors that are safer, such as face or fingerprint ID. One-time codes – sent via SMS or email – is another way of replacing traditional passwords. Many times, these methods are often a part of MFA as verification in addition to the user’s password.
Why Implement IAM?
Identity and Access Management reduces the likelihood of an attack by verifying users are legitimate and only accessing information they are authorized to. It protects areas including data, software, development platforms, organization devices, data centers, and integrations.
The way you do business is unique to you, and your security existence should reflect that. At Braxton-Grant, we work with a variety of partners; so, we can apply the best fit products and solutions for you.
Learn more: Our Identity and Access Management Solution Offerings


