Secure Web Gateway: What it is & Where it’s Going
Moving the Cloud: The SASE Puzzle Part 4
How is a Secure Web Gateway Defined Today?
A Secure Web Gateway (SWG) protects users and organizations from malicious activity when browsing the internet. The goal of a SWG is to inspect web traffic at the application level, while not compromising the user’s overall web experience. No matter the location of the employee on the network, the gateway’s role is to:
-
-
- Filter URL/content, anti-virus, and malware detection.
- Decrypt SSL traffic.
- Enforce web application controls.
-
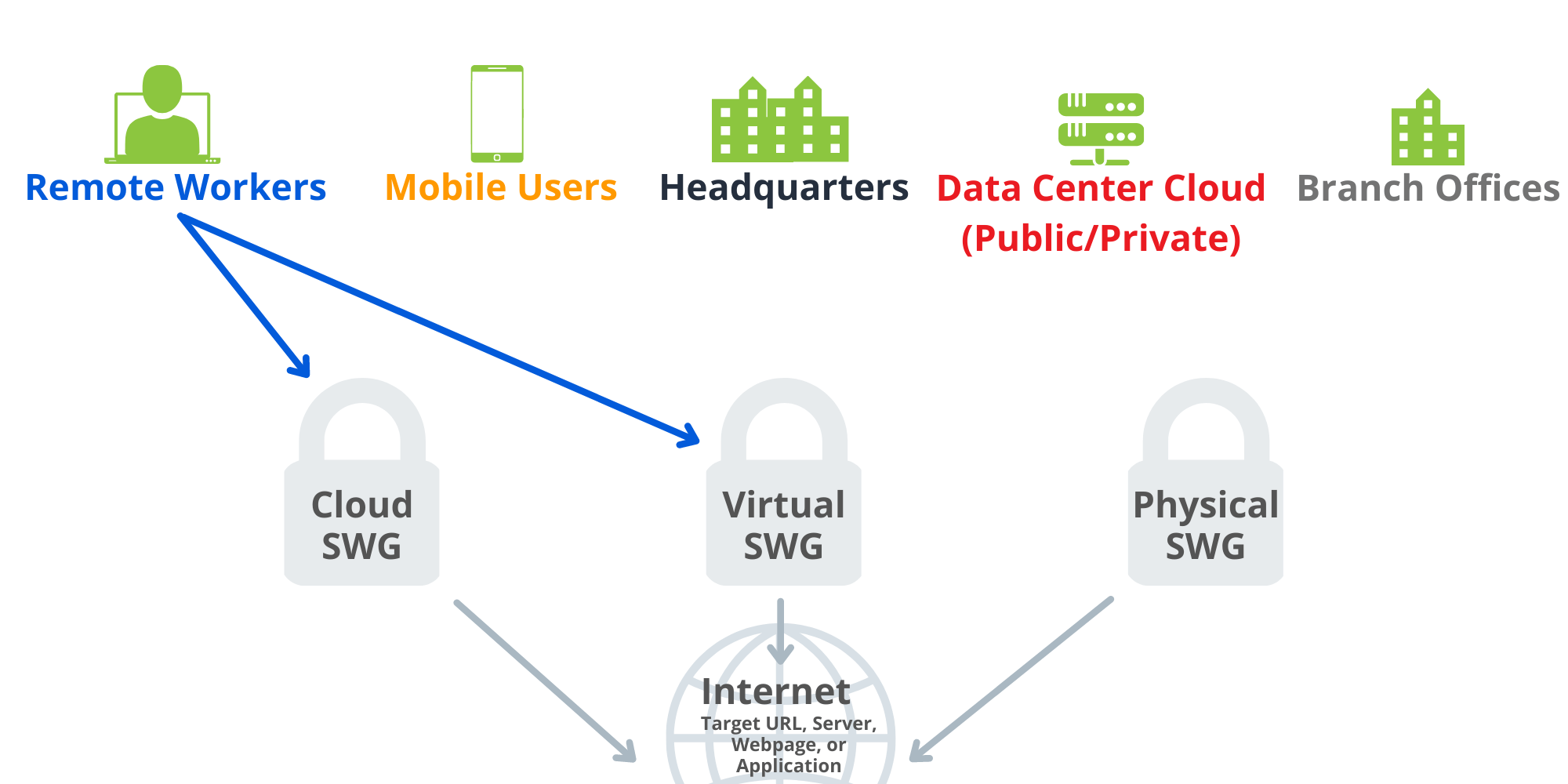
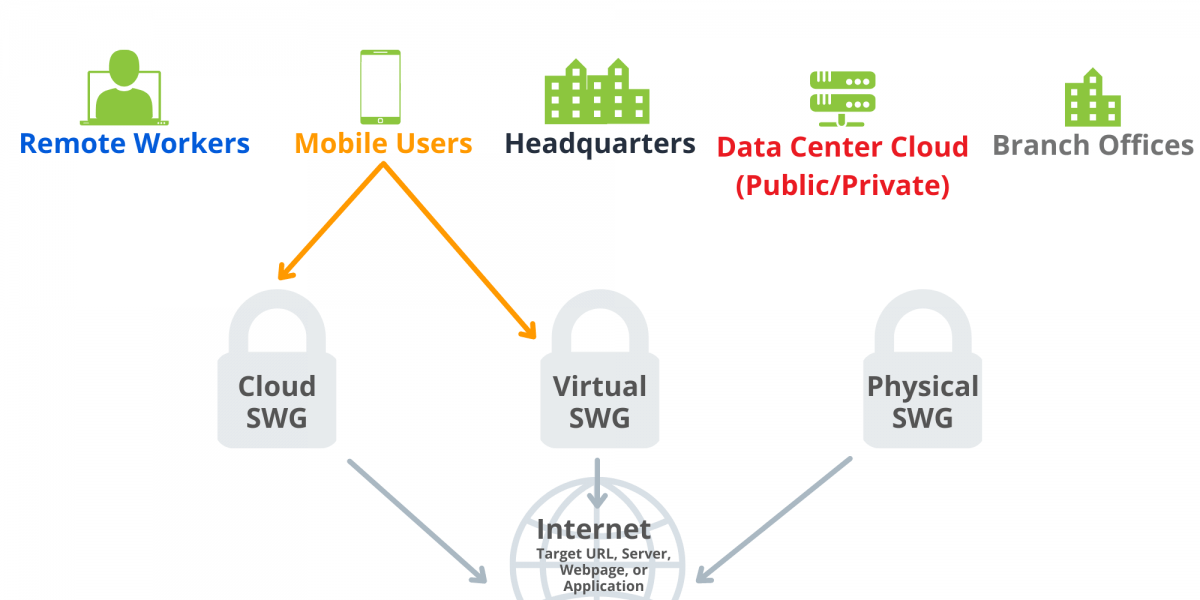
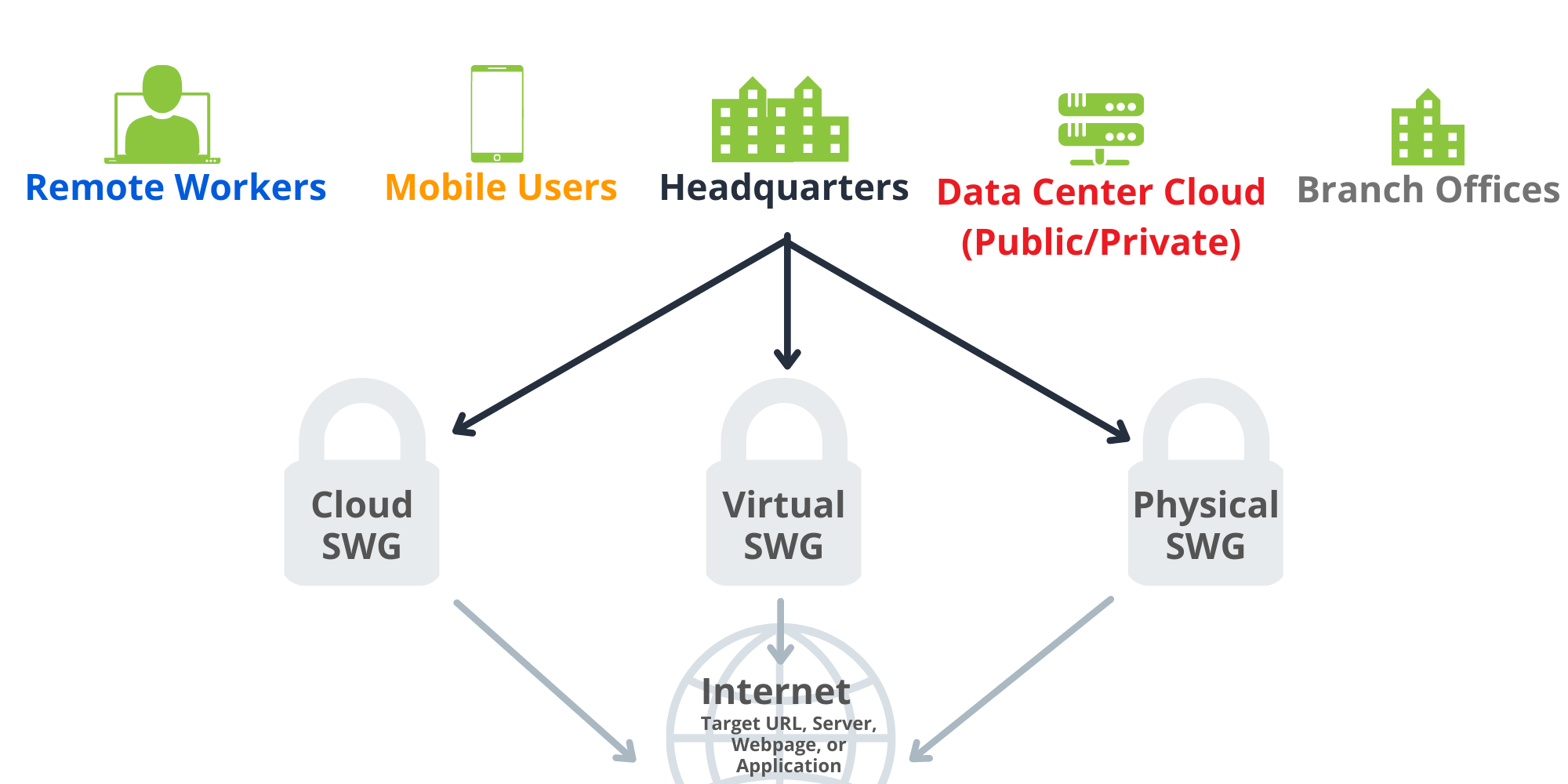
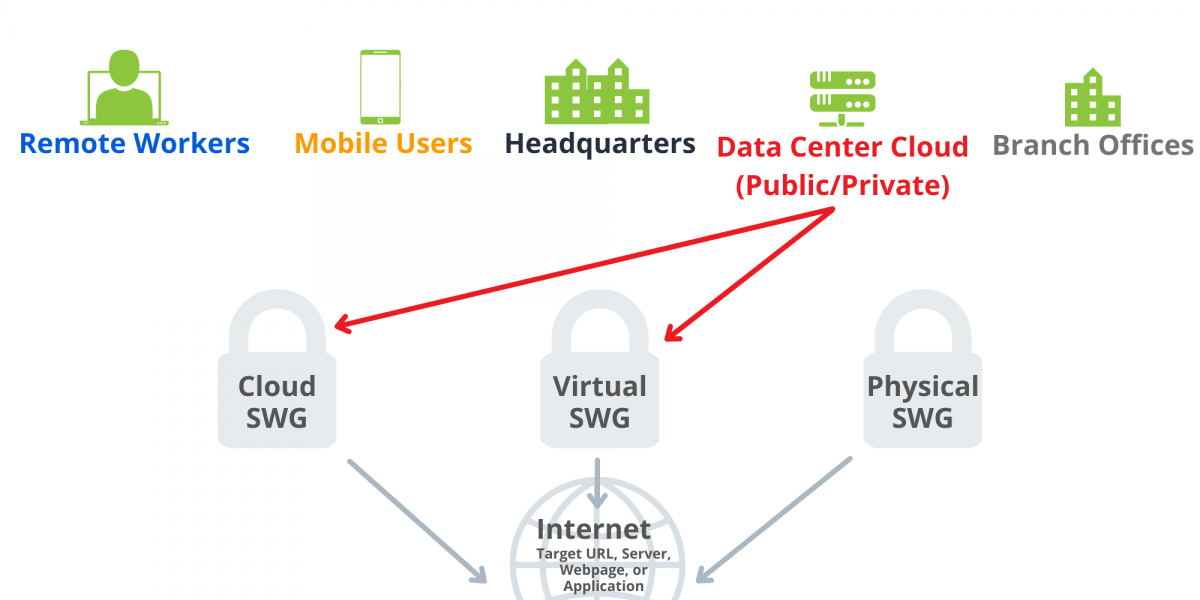
As user traffic now sources from work from home (WFH) or remote users, many of these SWG offerings must accommodate for a combination of corporate users and remote users; meaning, there is now the need to have SWG capabilities beyond just the local edge of the corporate headquarters, and a hybrid approach is necessary to protect all employees.
Gartner defines that, at minimum, SWG includes URL filtering, malicious-code detection and filtering, and application controls for popular web-based applications, such as instant messaging (IM).
Additional Capabilites
A SWG may also have the functionality to provide anti-virus (AV) scanning or Data Loss Prevention (DLP) capabilities from external sources, or in rare cases, with on-device policies. Web Isolation is another feature that may be offered; however, it is not considered a standard SWG function due to off-box integration or software license activation to use. Finally, the ability to offload a copy of the decrypted traffic could be included in SWG capabilities, but all these are traditionally add-on capabilities to the product and not part of the initial feature set.
How does a Secure Web Gateway Work?
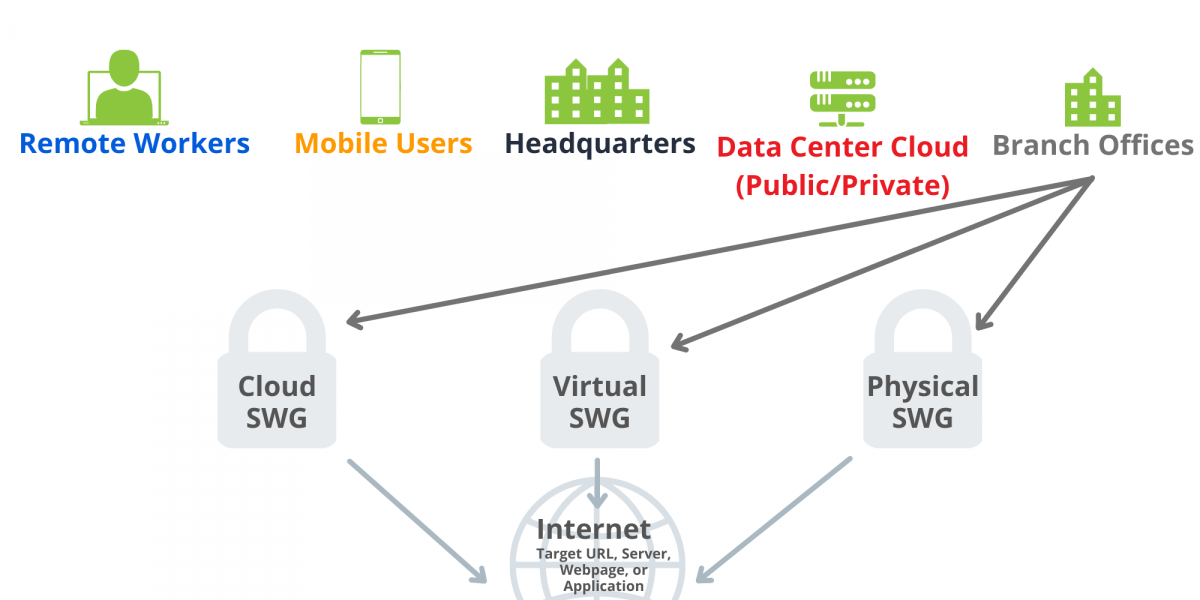
A SWG can be installed either as a software component, cloud-hostable virtual component, or as a hardware device. Attached to the edge of the network or at the user endpoint, it filters and monitors all traffic for malicious activity through web application use and attempted URL connections. Any activity that is not approved can be blocked or restricted. Blocked sites are usually stored in the SWG database, or when possible, sourced from intelligence feeds that are either company sourced or third-party provided.
Additionally, information flowing out of the network can be monitored. The SWG can perform logging on all your web traffic, combined with decryption of SSL web traffic for full visibility and user authentication. Overall, this gives you the ability to always know who is going where, proactively monitor the network and tweak policies as needed, and investigate prior events in case of attacks or vulnerabilities.
What Configuration is Applicable to your Organization?
What are the Benefits?
With a SWG, organizations can enforce company policies that prevent end users from visiting malicious sites, while also restricting the use of the internet to business-critical functions. Having these policies in place prevents malware infections and detect infected devices. Also, a SWG protects remote workers since security policies are always aligned, even when employees are not located in corporate headquarters.
SWG Requirements
SWG execution is flexible since it can be deployed inline, virtually inline (WCCP, PBR), or out-of-path (explicit proxy). Certain deployments will allow for ease of future growth, while some will be more limited. An inline deployment is an example of this, as there will be downtime necessary if the physical device requires maintenance or is not operating as expected.
It can also be used in a reverse scenario – to protect externally facing corporate web accessible resources to customers – but our focus today is focused on protecting users while accessing corporate assets that meet their day-to-day needs.
What Questions Should be Considered before Deploying a SWG?
Understanding the types of users, servers, or traffic that will need to be proxied helps your approach in authenticating what users are permitted to access.
Deciding the nature of the traffic and devices that are generating traffic will scope the devices that need permission to traverse without an inspection policy.
User location, corporate physical space, and use of the cloud for hosting are important to find before deciding the type of appliance that will meet your company’s needs. Future goals, such as migrating to a more hybrid environment, may also determine the speed in which adoption is needed.
An Acceptable Use Policy will help shape your organization’s policy building, as well as discussions with a governance group if enforcing DLP policies. It is possible that your company has acquired applications to enforce policies and prevent exfiltration of sensitive data, but the Acceptable Use Policy should be the administrative control identifying the technical controls that will be in place on the SWG.
Identify a process to handle exceptions and how to process the risk analysis review of that request to permit them to be bypassed, if necessary, from authentication or SSL decryption. Some devices or systems may be unauthenticated but still decryptable, while others may not allow for decryption or authentication.
Some vendors will provide global policy effectiveness, whether you have deployed your systems on-premises, through the cloud, or a mixed combination. Your organization may value a simple policy execution and look to identify vendor products where a single dashboard (a single pane of glass) view of policy and deployment is possible. Not all vendors provide such capabilities, and even vendors that provide such may not be able to extend every granular option that on-premises provided to the cloud. Research the right solution that meets your needs and leverage our expertise to match your needs with the perfect vendor product.
Connecting SWG to SASE and Cloud-Based Security
As a critical aspect of the SASE infrastructure, a SWG is strategically located in a position to monitor all web traffic, provide verbose logging, and prevent and detect attacks. Meanwhile, a SWG integrates with other technologies, such as a DLP or a sandbox, that require a SWG or similar device to feed it traffic.
Cloud Access Security Broker (CASB), a component of SASE and integration potential with Zero Trust, extends the traditional SWG to cover the more advanced internet web-hosted applications that we use today for mobile, desktop and abroad. CASB could be considered a SWG for the SaaS world has additional capabilities that the original SWG may not have been configured to support when it was originally deployed. The internet has changed, and the idea of what was available on the internet has evolved from static web pages to dynamic content and interactive applications.
Looking Forward – The Future of SWG
As the migration to having a cloud-first or hybrid solution for SWG continues, you’ll likely come across terms like Cloud Web Security Solution, Cloud Web Gateway, Cloud Delivered Web Gateway, or others. With the need to protect cloud storage, cloud hosted applications, and employees leveraging cloud-provided virtual desktops increases, the need to have a SWG protecting those resources is increased as well.
Cloud-based or cloud-hosted SWG allows for more flexibility in scaling and bandwidth demands, which would be an operating expense versus a capital expense. This may work better for a company that does not maintain the same traffic needs and demands each year. Moving away from physical purchases and hosting applications has already transitioned costs to more operational, and hence, hybrid or remote working environments no longer demand the previous capital spend of physical appliances as they once did.
The growth of cloud-based applications and services has not completely rendered the traditional SWG obsolete; however, it does means that a SWG is part of the defense in depth approach, as it was not explicitly designed to handle Cloud SaaS solutions or the heavily increasing mobile workforce. SWG combined with a Cloud Access Security Broker (CASB) allows for coverage of internet-bound web traffic as well as cloud hosted offerings.
In the future, expect to see SWG transition to being referred to as SSE, which stands for Security Service Edge.
At Braxton-Grant, we are a multi-vendor integrator that has deep experience in SWG implementation that you can leverage. Reach out to us today to get started today!