“Should I Switch to FWaas?”
Moving to the Cloud: The SASE Puzzle Part 6
A firewall is commonly known for monitoring incoming and outgoing network traffic, acting as a barrier to prevent unauthorized access. Previously, firewalls could be either hardware or software, but various forms of cloud adoption have forced firewalls to adapt to organizational change. Just think about how significantly your organization’s security has changed in the last three years (or in the case of 2020, less than three months). With every turn of events, your security must change as well. Enter firewall as a service (FWaaS), a critical component of SASE. FWaaS brings your firewall up to speed with the trending cloud environment.
What is FWaaS?
FWaaS is a cloud firewall that is avaliable anywhere (another term that may be used is Cloud Firewall Service, or CFS). The goal of this type of firewall is to not only eliminate the need for a physical appliance, but to also simplify your security environment and streamline company policies across in-office, remote, or hybrid workers. Gartner analyst Jeremy D-Hoinne defines FWaaS as “a firewall delivered as a cloud-based service or hybrid solution (that is, cloud plus on-premises appliances). The promise of FWaaS is to provide a simpler and more flexible architecture by leveraging centralized policy management, multiple enterprise firewall features and traffic tunneling to partially or fully move security inspections to a cloud infrastructure.”
Despite its simplicity, a cloud firewall still delivers next-generation firewall (NGFW) capabilities including URL filtering, advanced threat protection, intrusion prevention systems (IPS) and DNS security. The key advantage to this type of system is the scalability and versatility of it being avaliable anywhere, while still enforcing unified policies across and organization.
FWaaS vs. NGFW
Before FWaaS, the NGFW was the evolution of the traditional use of a firewall to expand and evolve past the tradition capabilities and roles. NGFW offerings have been adding features prior to the larger migration to the cloud, but the but the abilities they provide are also needs that FWaaS may be desired to fulfill also. The traditional roles of a firewall including packet filtering, stateful inspection, and VPN awareness are all supported in NGFW; yet, it also allows for potential application awareness and control, intrusion protection, threat intelligence, information feed support, DNS security, and new techniques for evolving security threats.
While both FWaaS and NFGW are replacing the image of a typical firewall, a NGFW is a firewall with advanced features, while FWaaS is a cloud-delivered firewall. Even though the two are often compared, a NGFW is about what the capabilities of the firewall are, while FWaaS is where the firewall is deployed; therefore, there can be a lot of overlap between the two. FWaaS can have NGFW capabilties and a NGFW can also be hosted on the cloud. It’s not just one or the other.
It can be broken down like this:
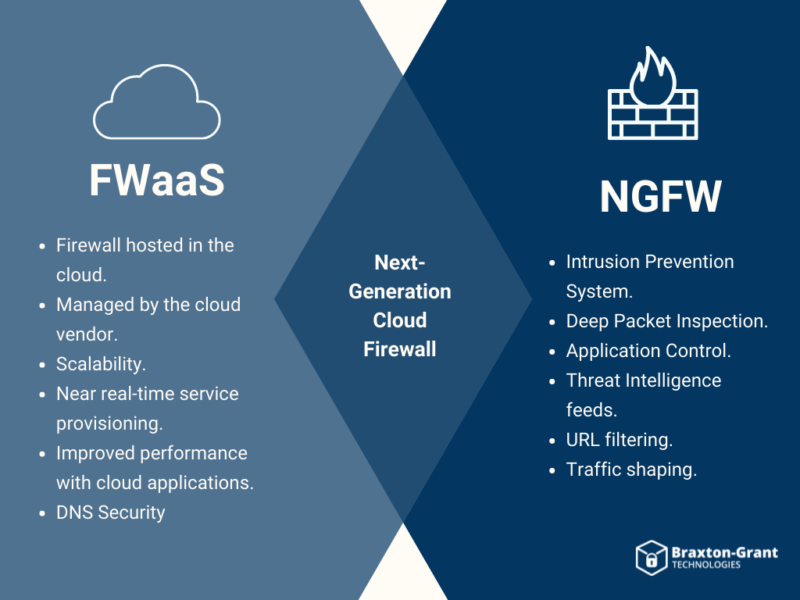
The key difference between FWaaS and NGFW is the FWaaS may be hosted by the vendor: where the vendor is required to configure, maintain, and update the OS or options provided to the customer. If a customer runs a NGFW in the cloud, they will be responsible for the configuration, maintenance, and updating of that software.
FWaaS is Different from your IaaS/PaaS
Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) are virtual firewalls in the cloud designed to protect your cloud infrastructure, but not specifically your remote users or network perimeter.
With IaaS/PaaS, your organization is “renting” the infrastructure from the service provider you have selected, where you create, provision, and manage your own virtual servers. You can use these servers for storage, applications, and more. In this environment, you need to protect these hosted offerings from malicious traffic or attacks, in addition to protecting them from other servers or insiders attempting to take control of a cloud–hosted server.
It is important to mention that virtual firewalls may also be used in your data center beyond just in the cloud. Just like we discussed with building your own servers, most vendors provide a product with a license option for IaaS/PaaS, and may or may not contain the same functions and features of the on-premise NGFW offering. This allows you to host that NGFW, either as a pre-provided virtual machine or run on an existing virtual machine. Do not be misled, the virtualized firewall has plenty of functions and features if you want to protect a grouping of servers or specific server with micro segmentation, but the configuration of these rules or policy relies on your team. Even if basic IaaS or PaaS offerings are allocated by the service provider you have selected, it is in your best interest to install and manage your own firewall to protect your hosted applications and the servers they reside on.
When is FWaaS Right for your Organization?
Let’s face it, for many companies, hardware firewalls are difficult to maintain from both a budgetary and operational standpoint. FWaaS gives all employees access to the same number of resources on several types of devices; hence, scalability is easier no matter the size of your organization.
-
- Do you find that you must hairpin your remote user traffic back to a branch or primary office to provide the security you need?
- Where does the majority of your user access sit – the Private/Public Cloud services or serviced from an internal hosted server?
- Do you want to reduce your management footprint and allow for improved scalability with a unified security policy?
- Is your firewall intended more for on-premise users and less for your shift to remote support users?
- Does your current firewall need to offer local and cloud integration for complete network visibility?
- Are you looking for a cloud provider who can offer protection against Distributed Denial–of– Service (DDoS)? (A DDoS attack is a malicious attempt to disrupt normal traffic of the targeted server, service, or network)
- Do you require control over versioning and updates to your firewall software as to test updates before they are released to production?
Connecting FWaaS to SASE and Cloud-Based Security
As a critical aspect of the SASE architecture, FWaaS brings together the protection of an on-premise solution while still being flexible enough to fit the modern workplace. For many companies, that means fading away from traditional, in-house options. Network edge has changed, so FWaaS adjusts to the flexibility and scalability that can’t be achieved with an appliance-based firewall. The best fit may be determining whether your current vendor has FWaaS offerings and evaluating whether the offering meets your cloud needs. FWaaS helps by providing the migration to the new network edge of your organization, the cloud, and integrating with the other components to complete a full SASE posture of connectivity.
FWaaS is also important to organizations working to meet the upcoming drive to the SSE Gartner Quadrant, which includes FWaaS and Software Defined Wide Area Network (SD-WAN). When including SD-WAN, it allows the ability to restructure your network security to meet the changing needs of your enterprise and users. SD-WAN benefits from being deployed in conjunction with FWaaS by receiving the integrated security offered by FWaaS. The partnership and combination of these two products allows a company to improve the performance and usability of their corporate WAN.
Implementing SASE correctly secures your workforce, no matter where they are. Choosing to partner with Braxton-Grant means we can become an extension of your team, work toward your goals, and be a trusted resource with deep experience that you can leverage.


