What is Workflow Automation?
Workflow automation replaces time-consuming manual tasks with software designed to execute many daily business processes automatically. Network administration, business operations and DevOps collaboration can be streamlined, resulting in cost-savings benefits for most organizations while reducing human error and processing time. Workflow automation improves communications and facilitates optimal use of employee time and company resources. Workflow inefficiencies and oversights can be eliminated by automating workflows.
10 Benefits of Workflow Automation
What Is Network Security Workflow Automation?
NEW! Solve Real Problems and Improve Efficiency with Network Security Automation Integration Developed by Braxton-Grant
The critical skill shortage of cybersecurity professionals today requires the development of new processes to make existing cybersecurity teams more efficient. The risk of burn-out and simply overwhelming staff with cumbersome daily tasks is a substantial issue for companies. Using an unprecedented approach developed by Braxton-Grant, common security tasks can be automated to be accomplished during normal business hours or on a custom schedule.
Braxton-Grant Technologies curated a groundbreaking integration capability solution between CA Automic Automation and API capable network security products. Our cyber engineers leverage certified knowledge and the open API offered by a variety of vendor cybersecurity tools to bring Workflow Automation to cybersecurity that has never been seen before. We can now expand workflow automation across any security tool with a RESTful API capability.
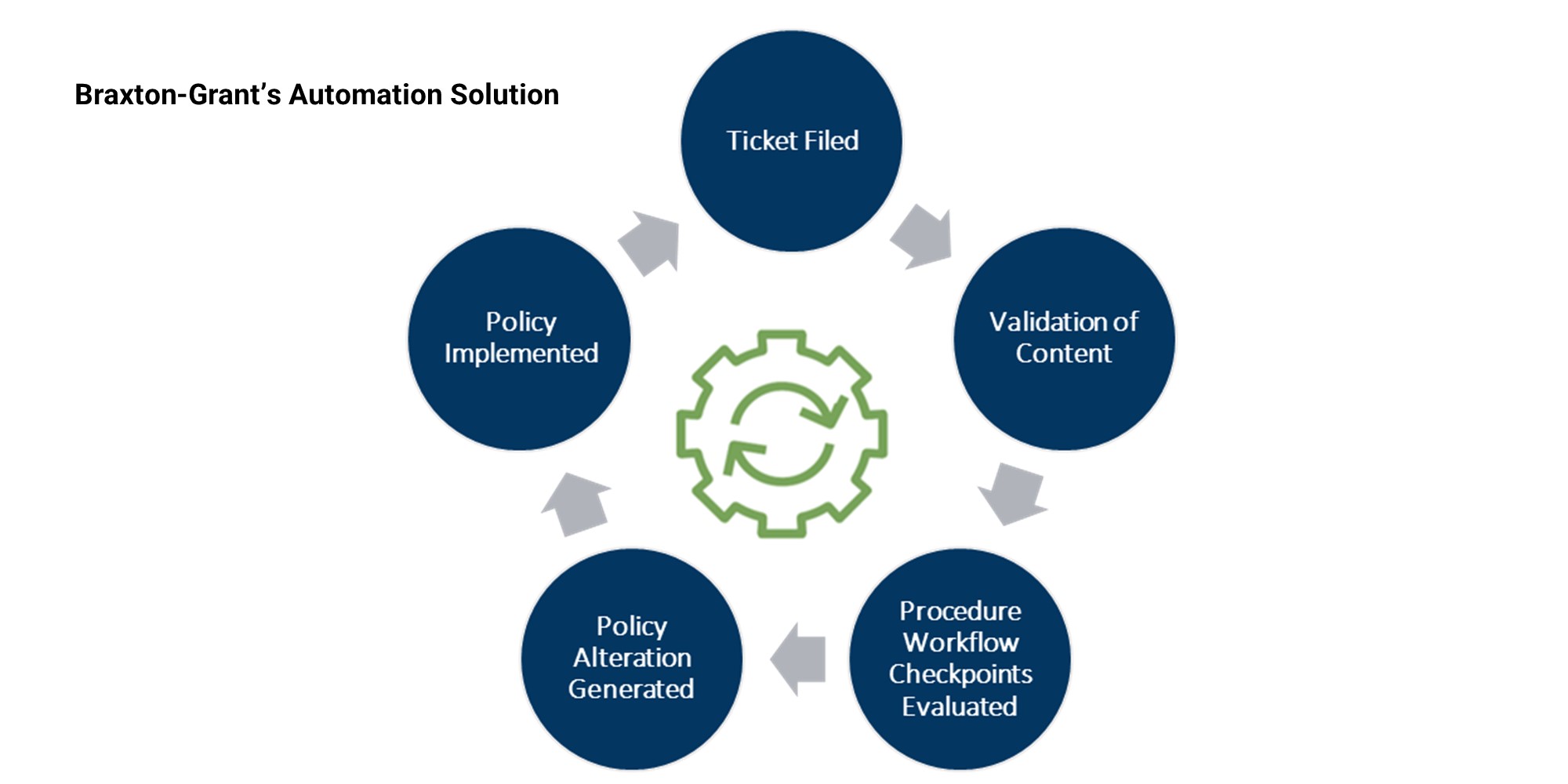
Examples of Automated Network Security Policy Tasks:
Policy Updates and Page Exception Use Cases
Proxy Software Upgrades/Patches
Use of Data Enrichment Feeds on Threat Sites and IPs
Scaling and Deploying/Decommissioning Virtual Proxies
Web Protection and Threat Feeds
Ingestion of External Threat Feeds sourced from internal subscriptions or 3rd party vendors
Deploy global policy to a variety of API capable vendor products at once in vendor-required formats, even in a multi-vendor environment
Network Automation promotes efficiency by reducing manual errors and employee workload, and improves security initiative delivery.
Cost Effectiveness and Improving Security Posture
Automate repeatable tasks for workday and after-hours scheduling
- Reduce chances of misplacement of policy elements which could provide security gap in policy
- Value for PLA or Value of Products Purchased (ROI)
True adoption of offered products, further investment in using all options available for a specific product, full product adoption and complete value delivery
Support Existing Automation Project
Augment an existing project with Best Practice knowledge
- Risk Avoidance
- Lessen Administrator errors in spelling/placement/policy creation
- Improved Cross-Product enrichment integration
Provide improved sharing of intelligence between Broadcom product suites such as: SAC/ZTNA, DLP, Security Analytics, SESC, WSS, EdgeSWG, CloudSOC, and other non-Broadcom Security platforms with API functionality such as iboss, Netskope, Forcepoint ONE, Palo Alto, Zscaler, Trellix, etc.
Extend Automation to other vendor tools without native Network Security Automation capability
How does Braxton-Grant help?
As a trusted IT advisor, we create the best solutions for you no matter where you are in the process of adding Automation to your security environment. Every company can simplify business operations with Workflow Automation and Network Security Automation to keep up with the modern workplace and maximize resources. We are here to implement quickly and identify and resolve hidden gaps in your network.
Where are you in the Process of Adding Workflow Automation?
Looking to use Automation to simplify to your processes? As a vendor agnostic certified reseller, we will…
- Assist in defining your organization’s Automation benefits.
- Identify vendor solutions based on your defined company or organization requirements.
- Design and recommend Workflow and Network Security Automation solutions to meet your specific requirements.
- Support POC evaluation and configuration as you evaluate possible vendors and solutions.
If you have some automation processes and components in place but would like to integrate more advanced automation capabilities, test and evaluate to finish the process, we . . .
- Understand organizational use case requirements.
- Define outstanding needs and recommend a path moving forward for the timeline that has been identified.
- Audit current products and configurations and assist in recommending any areas of improvement.
- Recommend vendors and solutions that will help you close the gap.
- Provide the help of experienced engineers to get you across the finish line.
Looking for a third-party review or need to validate your system with additional compliance? We will…
- Provide an audit of your current cybersecurity systems.
- Help you align with other compliance requirements such as NIST, CMMC, or HIPAA.
Not totally satisfied with your current solution’s performance? We will…
- Provide an audit on your current solution and make recommendations for improvement based on your findings.
- Recommend vendors that will better fit your needs.
Our Vendor Partners
The way you do business is unique to you, and your security existence should reflect that. No matter where you are in the world or whether you have employees on-premises, hybrid, or remote, we work with a variety of partners so we can apply the best products and solutions for you.



