What is Advanced Threat Protection?
Advanced Threat Protection (ATP) provides solutions to stop threats before they reach your employees and respond quickly when things go wrong. It prevents, detects, and notifies you of advanced threats, including through email, mobile, social, and desktop. The main goal of ATP is to provide security against new attacks that are specifically designed to surpass common security solutions.
The three primary goals of ATP are:
- Early detection
- Adequate Protection
- Response
Why ATP?
Enterprises that develop mature ATP capabilities can reduce their identity management costs, and more importantly, become significantly more agile in supporting new business initiatives.
Functions of a comprehensive ATP solution offer:
- Real-Time Visibility: This allows you to continuously monitor threats to stay ahead of them. The more real-time information you have, the better.
- Context of Alert: Context grants you the ability to prioritize threats appropriately.
- Data Awareness: Having a deep understanding of data’s value can determine the level of a threat.
Learn More about Braxton-Grant’s ATP Solution Offerings
Advanced Threat Protection Trends
The recent release of RaaS (Ransomware–as–a–Service) has caused a spike in ransomware attacks over the past year, mostly due to the wide availability and ease of access. Attackers no longer need to develop their own tools. They can now purchase them much like they would a SaaS (Software-as-a-Service), which makes it much easier to access and more cost-effective. This increase in ransomware availability/attacks requires even more protection from your security tools such as ATP.
Migration to hybrid working scenarios and work-from-home (WFH) has put more of the protection risk on the user corporate issued device, or personal device used to conduct business at the forefront of the target list. Employee systems are no longer physically located behind corporate established protection and network security devices, and the protection offered by cloud services are not always a one-for-one replacement of corporate network defense; meaning, protection with ATP components is even more important as the landscape of attack has re-focused to the end user. This doesn’t mean that end users weren’t always a valuable and vulnerable attack vector, but they weren’t as easily targeted when stationary behind a corporate network protection. When discussing the biggest challenges to these WFH employees, refreshing company security and remote policies – such as phishing and social engineering – encourages executing the practice of good cyber hygiene.
Key Components of ATP
(1) Email Security
Email security describes the techniques and functions intended to keep sensitive communication in email secure, preventing unauthorized access, loss, or compromise.
Email is a common area of malware, spam and phishing attacks. Email security often can involve the use of a Secure Email Gateway (SEG). Much like Secure Web Gateway (SWG), a SEG acts as a firewall between outsiders and your organization’s email accounts, protecting inbound and outbound communications.
Traditional methods to protect email accounts involve some of the same topics we aim to cover in our IAM Solution suite, including:
- Using strong passwords.
- Password rotation.
- Spam filters that include desktop or anti-spam applications.
You can also use a service provider that utilizes these same protections on an email server, encrypting and/or digitally signing the messages from or to a user’s email address. Vendors may also offer firewall and/or software-based spam filtering to protect the user from malicious, unsolicited or untrustworthy emails from reaching the user’s inbox.
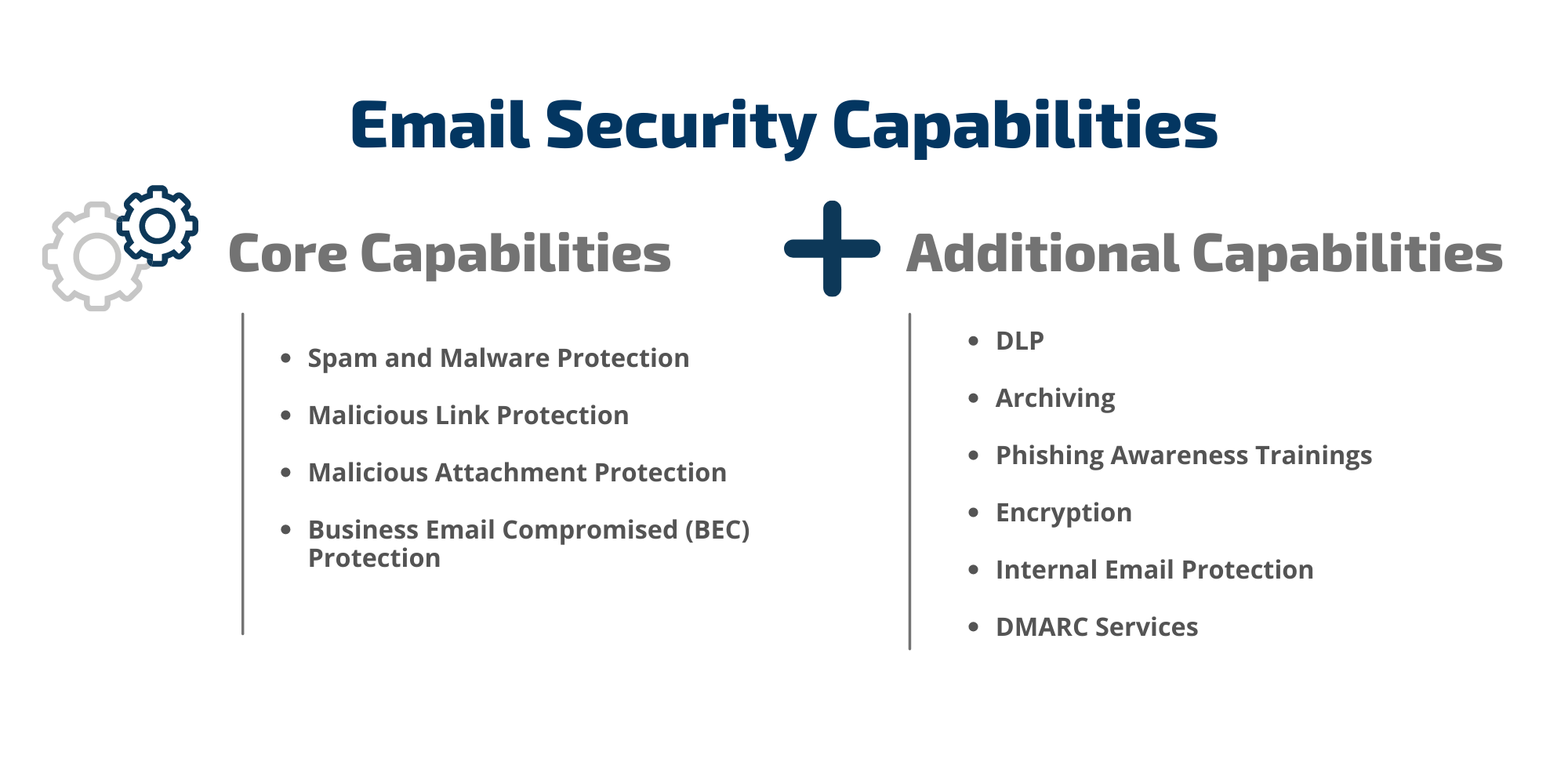
Using email security can protect your enterprise by:
- Controlling device access.
- Identify suspicious user behavior.
- Boost spam and phishing protection.
- Confidentiality of email communication maintained.
- Protect from zero-day threats.
- Real-time threat protection.
- Stop ransomware attacks, malicious URLs and weaponized attachments.
Ways to improve your email security:
- Backup Critical Files.
- Employee Education and Awareness Training.
- Automation of Email Encryption.
- Leveraging Sender Authentication standards.
- Using MFA.
- Adding security email gateway to your environment.
- Threat response procedure.
(2) Endpoint Detection Response
An Endpoint Detection Response (EDR) records and stores endpoint system-level behaviors, detects suspicious system behavior, provides contextual information, blocks malicious activity, and provides remediation suggestions to restore affected systems.
Required components for EDR include:
- Detect security incidents.
- Contain the incident at the endpoint.
- Investigate security incidents.
- Provide remediation guidance.
EDR has several benefits, including:
- Monitor endpoints and detect issues.
- Remediate present threats to endpoints.
- Investigate incidents to identify causes.
- Contain threats and restrict access to other endpoints or networks.
(3) Next Generation Firewall
A Next Generation Firewalls is an intrusion prevention system that includes advanced security features such as application control, threat intelligence feeds, URL filtering, and traffic shaping.
Read More: “Should I Switch to FWaaS?”
Defined by Gartner, a NGFW should have:
- Application Control
- User-Awareness
- Intrusion Detection
Functions of a comprehensive ATP solutions should offer:
- Real-Time Visibility
- Context of Alert
- Data Awareness
(4) Patch Management
Patch management distributes and applies updates to software. Ensuring your workstations, laptops, and services are properly patched prevents an estimate of 60% of successful attacks. This highlights the critical need to distribute, apply, and track software updates to your infrastructure.
The MITRE ATT&CK Model
The Mitre ATT&CK model (MITRE Adversarial Tactics, Techniques, and Common Knowledge) is often used to protect against the chain of attack. ATT&CK was created so the cybersecurity community had a knowledge base of techniques and sub-techniques to defend threats based on real-world observations.
Reference to the MITRE ATT&CK is often mentioned when looking at ATP solutions that address one or many aspects of this model based on cyber adversary behavior. The behavioral model presented by ATT&CK contains the following core components:
- Tactics denoting short-term, tactical adversary goals during an attack (the columns).
- Techniques describing how adversaries achieve tactical goals (the individual cells).
- Documented adversary usage of techniques and other metadata (linked to techniques).
Often vendor products that cover ATP will have some integration with ATT&CK to identify how that seen alert relates to a specific Category and or technique in the ATT&CK categories list.


